Understanding Symmetric Cryptography – Types and Applications
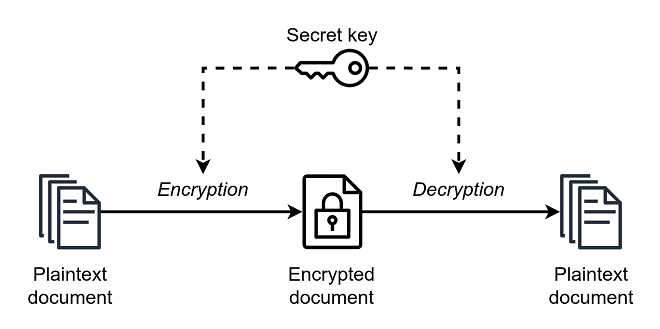
Symmetric encryption is part of virtually everything online, from logging into bank accounts to shopping online. It turns plain text into ciphertext so that only those parties with the shared key can read messages.
The same key is used to encrypt and decrypt data, which can pose challenges when a transmission channel is compromised. This article will examine some of the most common symmetric cryptography algorithms today.
Types of Encryption
Symmetric encryption uses a single, shared key to encrypt and decrypt data. It’s one of the most common types of encryption and can be used for a wide range of applications. For example, it’s part of PCI DSS compliance requirements for encrypting at-rest credit card payment data.
Also known as secret key cryptography, governments and militaries have long used symmetric encryption to protect confidential communications. It’s considered more secure than asymmetric encryption because it requires exchanging a secret key between communicating parties (and this key must be kept private).
To use a simple symmetric encryption example, if Claire wanted to share a confidential file with Jacqueline, she would encrypt it using her secret key and then send it to her. Then, if Jacqueline wished to view the file, she’d decrypt it with her private key.
The problem is that if the secret key is compromised, it’s easy for unauthorized parties to decrypt data and steal information. That’s why hiding the private key from unauthorized users is crucial. Furthermore, it would be best to learn some types of cryptography and what they are.
Stream Ciphers
A simple symmetric encryption process involves using the same key to encrypt and decrypt information. It is a popular method to protect data from unauthorized access and snooping from cybercriminals, hackers, or disgruntled employees.
There are two main categories of symmetric ciphers: block and stream ciphers. In a nutshell, a block cipher breaks down a plaintext message into blocks of fixed size and then converts each block with the key to ciphertext. On the other hand, a stream cipher encrypts information by converting each bit into plaintext one at a time with the key.
Stream ciphers are known for their speed and low complexity. They are easy to incorporate into modern programs and don’t require the kind of complex hardware that block ciphers do. However, their simplicity makes them vulnerable to attack and can be hacked.
One of the biggest challenges in symmetric encryption is exchanging a secret key. This is a problem because it must be distributed, managed, and stored securely. This is often done with the help of a public/private key pair, which can take a lot of work to manage. Another issue with symmetric encryption is requiring a single key for encryption and decryption. This can be problematic because it allows anyone with the key to intercept and interpret messages.
Block Ciphers
Often used with stream ciphers, block ciphers convert plaintext into ciphertext, one or more data blocks simultaneously. They rely on a secret key to encrypt and decrypt data. Because of this, symmetric encryption can be much faster than asymmetric encryption. However, it can also be more complex due to the need for a shared secret key. It’s vital that this key be secure and cannot be hacked.
This kind of encryption is commonly used in online banking and email. It is also used by the popular messaging apps WhatsApp and Signal to ensure that only the intended parties can read and decrypt messages.
Because symmetric encryption depends on the secret key, it must remain secure and private. The key must be known to the sender and recipient of the message so they can both encrypt and decrypt the information. This is why it is also called private-key cryptography or single-key cryptography.
Symmetric encryption is rapid, which makes it ideal for securing large amounts of data in bulk. It is also more straightforward and less resource-intensive than asymmetric encryption. This means that it is a good option for servers and cloud storage. There is a wide range of block ciphers in use today. Some of them are tweakable, meaning they can be modified to alter their operation modes by using a particular input called a “tweak” along with the key.
Key Exchange
When using symmetric encryption, several methods can be used to exchange the key between two entities. One of the most secure methods involves out-of-band procedures such as calling a phone number or sending a letter through traditional mail, meeting in person, etc. This method provides an extra layer of security because it is not possible for anyone to intercept the cryptographic keys being transferred over a network.
Once the key has been exchanged between the two entities, they can encrypt and decrypt data. This is done using the same secret key to encrypt and decrypt. The disadvantage of this approach is that if someone snoops on the transmission channel or intercepts the encrypted data, they will also have the key needed to decrypt the message.
This is why symmetric encryption must be combined with another technique, such as authentication or digital signatures, to provide additional security. This helps prevent attackers from accessing the private key and decrypting messages or spoofing the sender.
Symmetric encryption is commonly used in banking-related transactions to protect personally identifiable information (PII) and payment card data from unauthorized access. This is important because it mitigates the risks of unauthorized activities such as identity theft and fraud and enables organizations to meet compliance requirements, like those set by PCI DSS (Payment Card Industry Data Security Standard), which requires them to protect at-rest cardholder data.





